1. Capture user and business requirements
2. Identify design constraints regarding security
3. Define system requirements
4. Draft or choose a starting system architecture
5. Evaluate possible solutions
b) Main activities
Document the requirements, this include targeted security level, regulatory environment, intended distribution area user requirements.
User requirements, includes security measurements/ requirements. The expected outcome should be detailed enough to abstract features for agile development.
Identify design constraints regarding security; from best practices and sector recommendations constraints can be derived that feed into the creation of system requirements.
Create system requirements defining performance assumptions and hardware boundaries
A system architecture is chosen, adapted or defined. The to be developed product or software is expected to function in a certain environment/architecture, for the purpose of simplicity only essential parts of the architecture are described or chosen. Essential parts are e.g. Interface, communication, security.
After a basic layout of the system is known a first security scan can be performed using the STRIDE Model early awareness of security issues will increase overall security of the end product at minimal additional cost. (The 2019 State of DevOps Report, presented by Puppet, CircleCI and Splunk)
Based on the available information possible solutions are discussed, and a first selection is made, this including e.g. tools, components, development environment. These decisions are captured in a design output document.
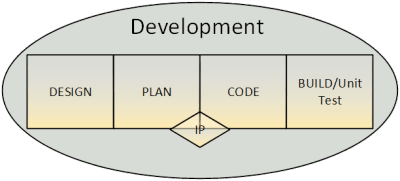
Goal: create and agree upon a feasible planning for the creation of the product/software.
Purpose: Agree upon a planning and the deliverables for a first increment
Main activities
The Design Phase should deliver a general understanding of to be developed product including some rough high-level requirements, some functional component descriptions, security issues and development direction (used tools and software environment). A product owner and development teams should now have enough information to define and describe stories and features for the first increment. Any missing info or requirements can be further detailed in a sprint. There are no specific tools for this phase. But several tools are available e.g. trello, (trello.com).
From a security point of view the attention point are “include planning for security”on top of the feature planning.
Goal: agile development of software modules to be used or integrated with chosen hardware
Purpose: Create software modules that fulfil the set stories and features
Main activities
Converts stories into code, captures tests and requirements in code or in separate documents. Agree on a coding standard, Code is to be made compliant to that. Coding analysis tools can be used.
Multiple sprints construct the prototype (software + documentation). Software is continuously compiled in the Build phase and compiler errors are corrected before a next build is scheduled.
1. Realized system requirements, solved defects and security breaches are documented.
2. A trace back to constraints and requirements is documented
Goal: compile created software modules, check for compiler errors, and know security issues in used libraries.
Purpose: Create executable safe software modules that fulfil the set stories and features.
Main activities
This process is largely automated, only if a build failed a message is send out to the configuration manager then first priority will be to repair the build. Included in the build phase are code analysis, code coverage and automated test cases. The results are captured in a build report, the build report is checked and identified issues will be put on the backlog, Issues can vary from lack of code coverage to potential security issues in the code or libraries. The build process is executed on the main branch, Builds of sub branches not merged with the main branch are out of scope.